The npm blog has been discontinued.
Updates from the npm team are now published on the GitHub Blog and the GitHub Changelog.
Three new features to help our users protect themselves
As you’ve probably noticed, npm has been on a roll delivering security features. We have three new features on the website that we’d like to share: the report a vulnerability button, security advisories, and a feature that prevents the use of compromised passwords.
Report a vulnerability
The rapidly growing number of packages in the npm Registry requires us to have a vigilant community who can report anything suspicious. If you feel like you’ve found a security flaw or a malicious module in the Registry, it’s easy to let us know:

On each package page there is now a “Report a Vulnerability” button. Press it and fill out the required information and we’ll decide whether to take action.
Please note: there is no need to send us the output of npm audit as we already know about those vulnerabilities. Take a look at the About security audits documentation to learn about the output of npm audit.
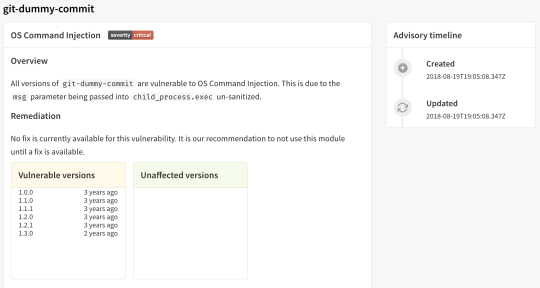
Improved Security Advisories
Security advisories are what power npm audit. They give you a brief overview of the vulnerabilities in a package, how we recommend you respond, and some handy reference links to find out more.
Transitioning the Node Security Platform required us to move the security advisories to npmjs.com so we took that opportunity to improve their look and feel. We also added a detailed timeline for future advisories so you can learn what changed and when during an advisory’s lifecycle.
You can find a sorted list of advisories on the advisories page.
Blocking password reuse of compromised credentials
It’s fairly common for users to reuse passwords between accounts, but it’s an extremely risky practice that should be avoided. If a shared password is used on another account that is caught in a data breach, attackers can use this public data to guess their way into the user’s npm account and other accounts.
When you sign up for npm or change your password, your chosen password’s hash will be compared against an enormous list of 571 million password hashes graciously provided by Troy Hunt and the Have I Been Pwned project.
If a match is found, you will be presented with an error and will not be allowed to use the password.

Don’t worry! We aren’t sending your password to a third party service. We keep it local to our infrastructure and we don’t transfer or store it in clear text.
Other ways you can protect your account
A great companion to a strong password is 2-Factor Authentication. If you haven’t yet enabled it for your account, we encourage you to take a few seconds to do this. Once enabled, make sure to keep track of your recovery codes in a safe place like a password manager.
We hope you enjoy the new security features we’re continuing to release. If you have any feedback join the discussion at npm.community.