The npm blog has been discontinued.
Updates from the npm team are now published on the GitHub Blog and the GitHub Changelog.
npm Enterprise: Delivering More Secure JavaScript Development
In March of this year, we launched npm Enterprise, our flagship product designed for large organizations and mission-critical projects. Today, we’re very pleased to announce the first major update to npmE, delivering a rich set of new security, compliance, and developer experience features our enterprise customers have asked for. This is just the beginning — we’re getting great feedback from customers on what they need, and work is underway on many new features that we’ll announce here soon. Meanwhile, here are a few that have just started shipping.
Security and Package Filtering
Our dedicated, vigilant npm security team evaluates packages in the public registry, assigning a vulnerability rating to classify how critical a security issue is. This rating was first made visible to users in npm@6 with the npm audit command and made actionable in npm 6.1.0 with the npm audit fix command.
npm Enterprise takes this protection a step further with the release of enterprise-wide security policies. Administrators may now choose a maximum vulnerability level allowed for all in-house JavaScript projects (Figure 1).
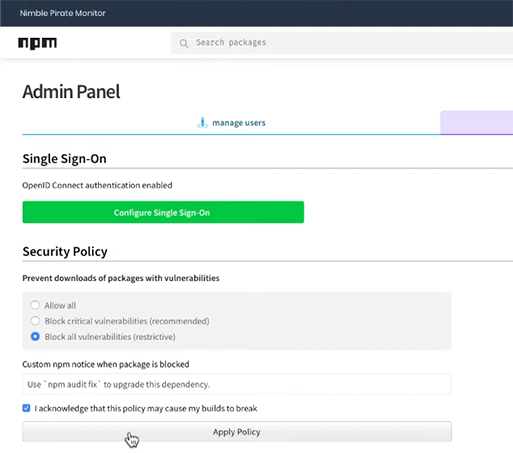
Figure 1: package filtering policy controls
When applied, the security policy will automatically filter out any packages that don’t meet security requirements, causing the npm install command to fail with a custom message to developers for all projects that use such packages (Figure 2). In many cases, it’s as simple as running npm audit fix to avoid using offending packages.
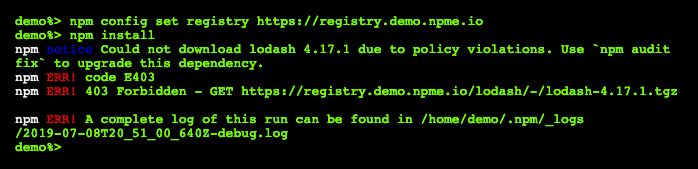
Figure 2: package filtering in the CLI
The security policies now available in npm Enterprise offer an extra layer of protection at the beginning of the software development lifecycle - when security issues are easiest and cheapest to fix - rather than further along the CI/CD pipeline or, in the worst case, allowing vulnerable packages into production software.
Watch a demonstration of package filtering in action ›
Vulnerability Reports.
Also building on the work of the npm security team, we are rolling out organization-specific vulnerability reports. These will be available initially as a beta for select Enterprise customers. These reports provide a detailed analysis of packages that have been acquired from the public registry by your organization’s developers. The reports reveal potential security threats you may have been exposed to, identify potential patterns in your package usage, and divulge when users make unfiltered requests directly from the public registry.
Sign up for the beta program ›
User Management and SSO
We’ve improved on the single-sign-on capabilities we introduced in the initial product launch. Now, we’ve broadened our SSO to include SAML support in addition to OpenID Connect, enabling npm Enterprise customers to on-board, off-board, and authenticate users with existing user-management infrastructure rather than maintain a separate set of user accounts which often runs into the thousands across multiple teams.
For those shops that can’t use OpenID Connect, we have also broadened our SSO capabilities to include SAML support. Between OpenID Connect and SAML, npm Enterprise SSO now covers the authentication requirements of the majority of large organizations.
Watch for more exciting solutions coming soon to help you and your teams succeed with JavaScript and npm. In the meantime, we’d love to hear more about what you think about our latest releases and what else you’d like to see in the future. And sign up below for our new CTO and Node.js Enterprise Advisory Group lead Ahmad Nassri’s webinar on Enterprise JavaScript done right.