The npm blog has been discontinued.
Updates from the npm team are now published on the GitHub Blog and the GitHub Changelog.
npm Security Insights API Preview Part 2: Malware
This is the second in a series of blog posts we’re running to preview and gather input on the new security insights API we’re developing.
Today’s topic: malware.
For years npm has maintained the most complete corpus of malware published on the npm Registry. We have meticulously curated it, cataloging which files contain the malware payload, integrity hashes, hostnames, IPs, URLs, and other related indicators of compromise (IOC).
Malware Corpus by the Numbers
Let’s take a look at some stats about our historical malware corpus:
- 302 malware packages, 463 individual package versions combinations.
- Top 3 payload locations:
- package/index.js
- package/update.js
- package/package-setup.js
- Most popular infection method: install scripts (> 2X payloads executed at runtime)
- we’re seeing that change as attacks grow more sophisticated
- Obfuscated/encrypted payloads: just 12% of historical samples
What to Look for in the API
Historically we have not redistributed malware once it’s discovered, but that is likely to change soon. This last week, we spent time integrating our malware corpus into the new security insights API that will provide access to use and learn from this data.
What data might be available?
- historical malware package source code
- payload details, such as the location, hash and if it was obfuscated or encrypted
- indicators of compromise such as hostnames, IP addresses, URLs as well as names, locations, hashes of dropped files
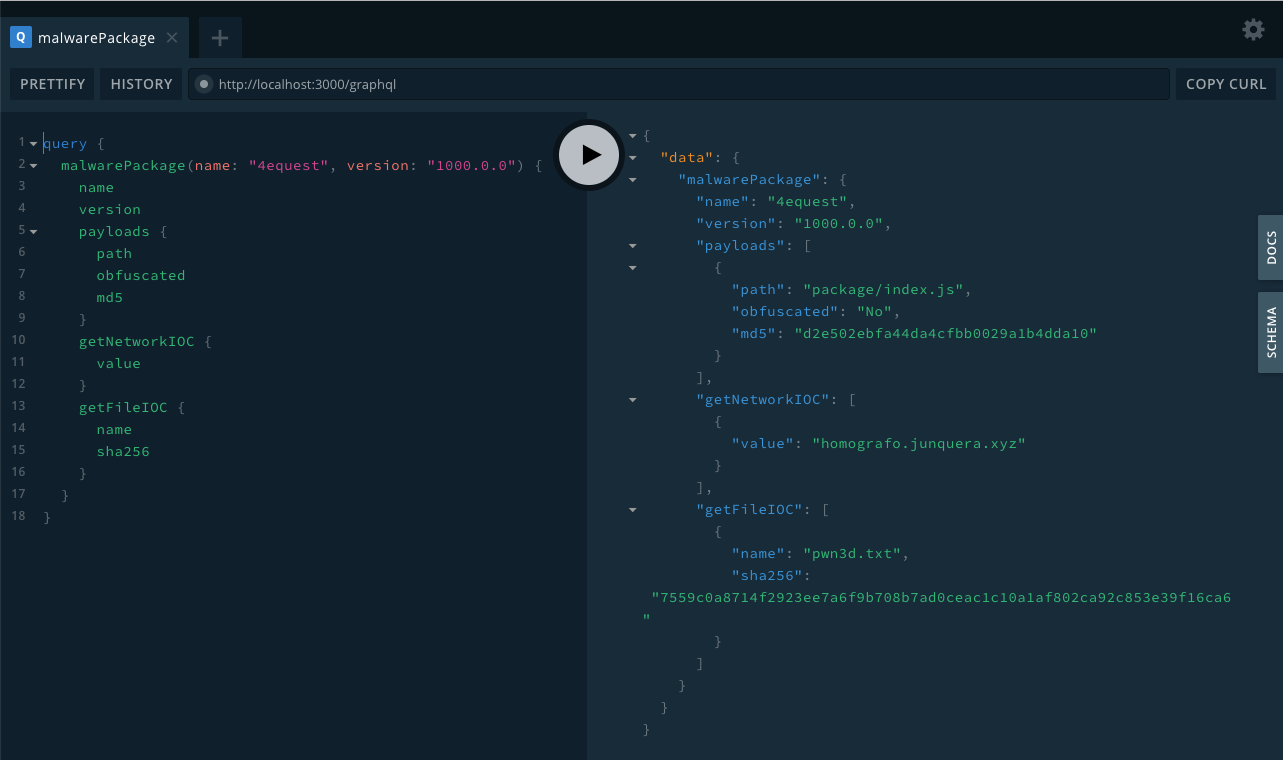
Example response from the new insights API
Possible uses of this data?
We expect the availability of this data to enable a lot of interesting research around JavaScript ecosystem malware, but the most obvious thing this will enable is for improved incident response. Using the various indicators of compromise, you can search your own environment for dropped files, hostnames, etc.
Update: Signups for the private beta are now closed.